RADIUS authentication starts when the user requests access to a network resource through the Remote Access Server (RAS). The user submits a username and a password, which are encrypted by the RADIUS server before being sent through the authentication process. The request may also include additional user information, such as location or network address.
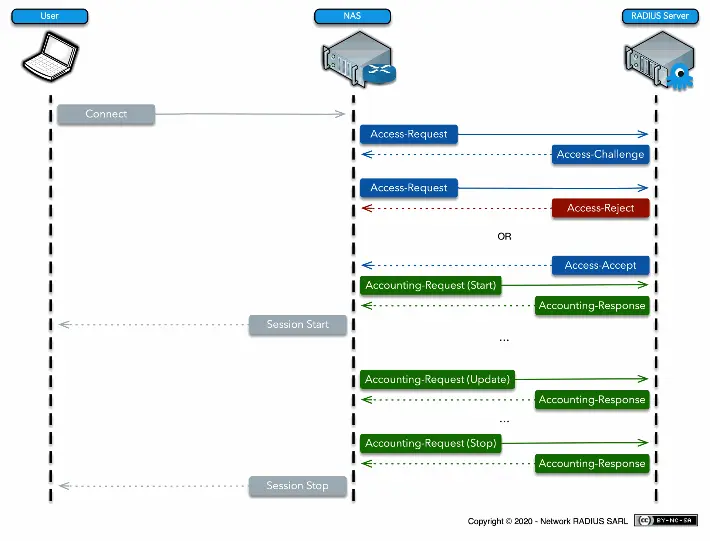
The RADIUS server then checks the accuracy of the information sent by the user. The RADIUS server employs authentication schemes to verify the data, either checking the user-provided information against a locally stored file database or referring to external sources such as Active Directory servers.
The RADIUS server may respond in one of three ways:
- Access Accept means the user is granted access to the RADIUS server. Each individual user may be granted restricted access without affecting other users.
- Access Challenge means that the RADIUS server will request additional information from the user to further verify the user ID. This additional information may be in the form of a PIN, a secondary password, or a card.
- Access Reject means that the user is unconditionally denied all access to the RADIUS protocol.
Need more help?
InkBridge Networks has been at the forefront of network security for over two decades, tackling complex challenges across various protocols and infrastructures. Our team of seasoned experts has encountered and solved nearly every conceivable network security issue. If you're looking for insights from the architects behind some of the internet's most foundational authentication systems, you can request a quote for network security solutions here.
Related Articles

Authentication: Is it really you?
RADIUS security is composed of three components: authentication, authorization, and accounting. These three links in the RADIUS security chain are often referred to by their acronym, “AAA”. The first of these, authentication, is the process that determines whether a client (a person, a device, or a software process) is a legitimate user of the system.

How does RADIUS Accounting work?
RADIUS accounting is a critical component of the RADIUS protocol that collects data for statistical purposes, network monitoring, and accurate billing of users. This process works alongside RADIUS authentication and authorisation to create a comprehensive network security solution.