The final step to configuring EAP for FreeRADIUS is to add the CA (Certificate Authority) to every client machine that performs EAP authentication.
Before proceeding with this step, make sure that you have already done the following:
- Configured and tested PAP
- Tested EAP configuration with dummy certificates
- Troubleshooted any problems with your EAP configuration
- Created production certificates and tested them
If you have done all of these steps, you are ready to go ahead with adding the CA certificate to all the client machines.
The simplest way to do this is to copy the file ca.der file from the /etc/raddb/certs directory to Windows desktop, and then double-click on it. This should start the process of importing the certificate into the Windows certificate store.
If double-clicking on the file does not work, see the EAP-TLS Howto on the main FreeRADIUS site for more detailed instructions, with screenshots. That document calls the CA certificate root.der rather than ca.der, but it has the same meaning.
Once the ca.der file is imported onto the client system, ensure that the Verify server’s identity by validating the certificate option is checked in the 802.1X supplicant (e.g. Windows laptop). Other supplicants (e.g. Mac OSX, or wpa_supplicant) use different methods for configuring a known certificate. See their documentation for more information.
Note: if you would prefer a command line tool instead of clicking through windows, see Command line testing for EAP configuration.
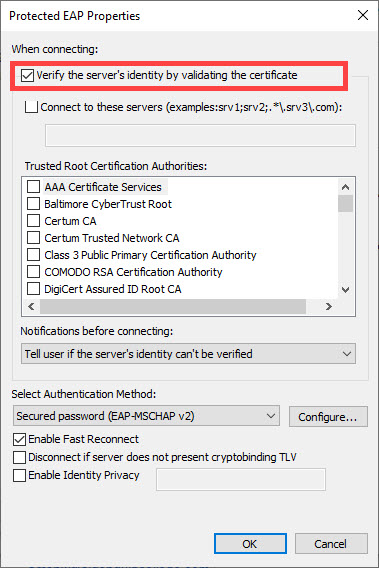
For a step-by-step walk through of how to get to this window, see our guide to EAP configuration.
Then, login using the user name and password from the PAP howto. (Which we assume you have already followed.) If all goes well, the server should send back an Access-Accept packet.
When the above method is used, the following authentication types should just work:
- PEAPv0
-
- EAP-GTC
- EAP-MSCHAPv2
- EAP-TTLS
-
- PAP
- CHAP
- MS-CHAP
- EAP-MD5
- EAP-MSCHAPv2
At this point, there are only a few things that can go wrong. See the EAP problems page for some common problems and solutions.
If everything works, then congratulations, you have
successfully configured the hardest parts of EAP authentication. If you
are still struggling after following all these steps, consider posting
your issues to the FreeRADIUS users mailing list.
Need more help?
InkBridge Networks has been at the forefront of network security for over two decades, tackling complex challenges across various protocols and infrastructures. Our team of seasoned experts has encountered and solved nearly every conceivable network security issue. If you're looking for insights from the architects behind some of the internet's most foundational authentication systems, you can request a quote for network security solutions here.
Related Articles

Configuring FreeRADIUS authentication with PAP (Password Authentication Protocol)
Password Authentication Protocol (PAP) is one of the most fundamental authentication methods used in Remote Authentication Dial-In User Service (RADIUS). Despite being one of the oldest authentication protocols, PAP remains an essential starting point for configuring your authentication server properly.

How to connect FreeRADIUS to Active Directory for authentication
Active Directory is widely used in the enterprise and university systems. This article describes how to connect FreeRADIUS with Active Directory, allowing you to authenticate users against your existing directory service while leveraging the power of your RADIUS server for network access control.